What is Kubernetes?
K8s is shorthand for "Kubernetes," which is an open-source platform for automating deployment, scaling, and management of containerized applications. It provides a way to manage multiple containers as a single unit, known as a "pod," and can be used to run, deploy, and manage containerized applications in a cluster of machines.
Why use Kubernetes?
K8s help in many tasks, some of the key features of K8s are:-
Container orchestration: K8s enables the deployment, scaling, and management of containerized applications, making it easier for developers to build, deploy, and manage their applications in a production environment.
Automated scaling: K8s can automatically scale resources (e.g. CPU, memory, and storage) based on the needs of the applications, ensuring that resources are used efficiently and cost-effectively.
Load balancing: K8s can automatically distribute incoming traffic across multiple replicas of an application, providing high availability and resilience against failures.
Self-healing: K8s can automatically detect and recover from failures, ensuring that applications are highly available and always running.
Configuration management: K8s provides a centralized way to manage and store configuration information, making it easier to manage complex application deployments.
K8s Architecture
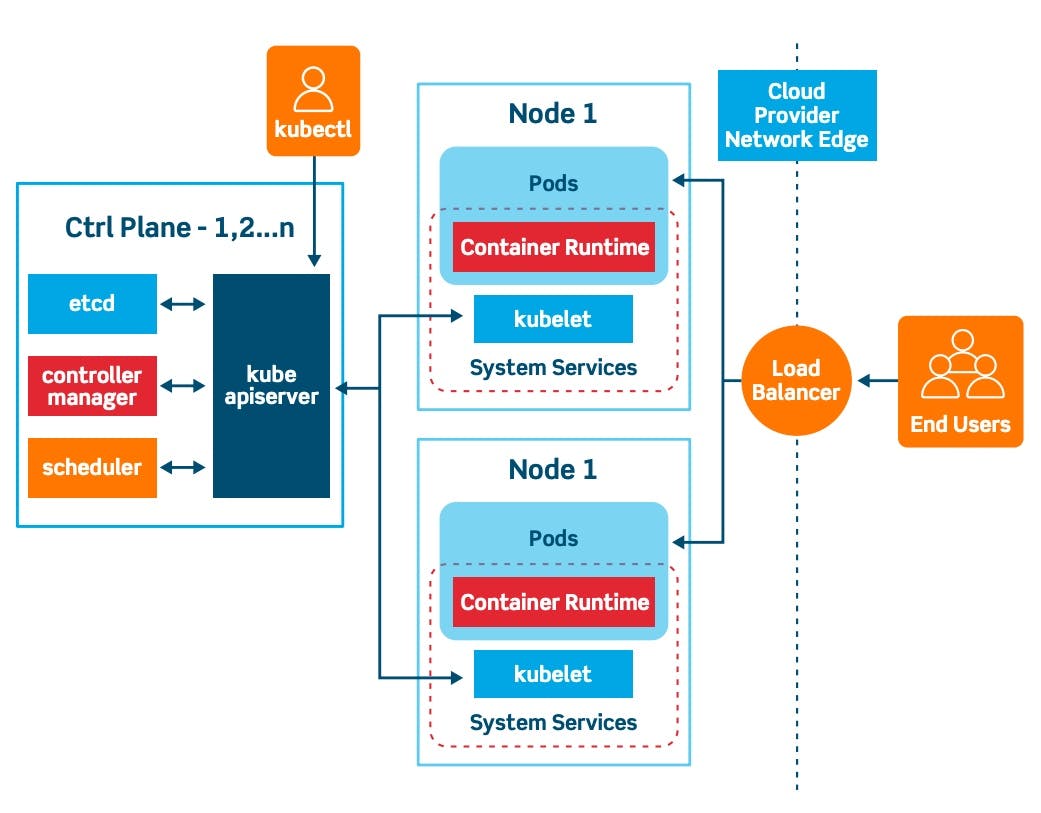
K8s Architecture mainly consists of 2 components Control Plane(Also called Master Node before) and Worker nodes. We communicate with the Control Plane through the CLI of K8s called kubectl. Control Plane divided the traffic and schedules the pods, pods are situated in the worker node, So we can say the worker node is where the application is going to run and the control plane is going to manage the worker nodes. Now Let's Discuss Each Component of the Control Plane and Worker Nodes.
Control Plane
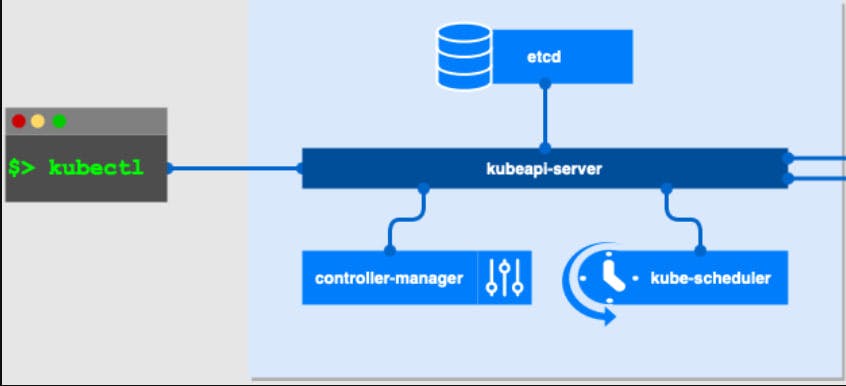
The Control Plane refers to a set of components that manage the state of the cluster and enforce the desired state of the system. The control plane components are responsible for maintaining the overall health and stability of the cluster and ensuring that the desired state of the system is maintained.
Components of Control Plane
API Server
The API Server is the central component that exposes the K8s API and serves as the front end for all cluster operations. It processes REST operations and acts as a bridge between the control plane and the etcd store. The API Server is responsible for maintaining the overall state of the cluster, including the current state of all objects such as Pods, Services, and Deployments.
etcd
etcd is a distributed, consistent key-value store used to store the configuration data for the cluster. It serves as the primary datastore for the cluster and holds all the information about the state of the system, including the current state of all objects. etcd is designed to be highly available, meaning that even if a node fails, the data stored in etcd is still available to the remaining nodes.
Controller Manager
The Controller Manager is a component that runs various controllers such as Replication Controller, Endpoint Controller, Namespace Controller, Node Controller, Service Account and Token Controllers and others, which handle routine tasks such as replicating Pods, managing node health, and handling endpoints. The Controller Manager is responsible for maintaining the desired state of the system and ensuring that any deviations from the desired state are corrected.
Scheduler
The Scheduler is responsible for assigning Pods to nodes based on resource availability and other constraints. It determines the best node to run a Pod on and ensures that the resources required by the Pod are available on the chosen node. But the Scheduler only decides on which node the pod should be scheduled but the component which actually schedules the pod and starts the pod on the node is called KUBELET.
Worker Node
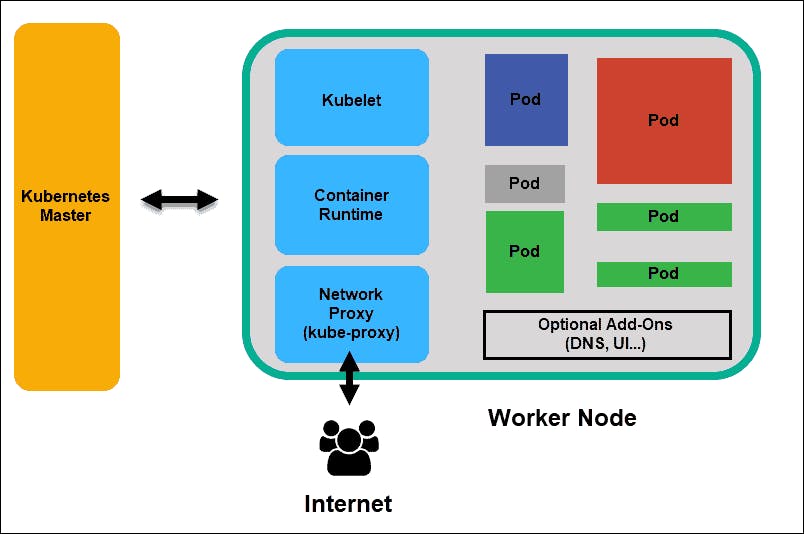
The worker node is responsible for executing and managing the containers that make up the applications in a cluster. It does this by performing many tasks such as Container Scheduling, Container Execution and Networking with the help of different components. It works closely with the control plane components to ensure that containers are running correctly and that the desired state of the system is maintained.
Components of Worker Node
Container runtime
A container runtime is software that runs containers on a node. Common container runtimes include Docker and rkt. The container runtime is responsible for starting and stopping containers, monitoring the health of containers, and reporting the status of containers to the control plane.
Kubelet
The Kubelet is the primary agent running on each worker node. It communicates with the API server to receive commands to execute and reports the status of the node and its containers. The Kubelet is responsible for starting and stopping containers, managing volumes, and reporting the resource usage of the node to the control plane.
kube-proxy
The kube-proxy is a network proxy that runs on each worker node. It is responsible for implementing the Kubernetes network model, which includes configuring network routes and enforcing network policies.
or in simple language
Since many applications are running inside the node, so if any application replica is making a request for a database, instead of the service randomly forwarding the request to any replica it actually forwards it to the replica that is running on the same node that initiated the request.
Pods
Pods are the smallest and simplest deployable units in Kubernetes. They represent a single instance of a running process in the cluster. A pod contains one or more containers, and all containers in a pod run on the same node and share the same network namespace. This means that they can communicate with each other using localhost, and share the same IP address, hostname, and network resources.
Container network interface (CNI)
The CNI is a pluggable interface for connecting containers to a network. The CNI provides the necessary network configuration for containers, such as assigning IP addresses and configuring network routes
Components of Kubernetes
1. Services
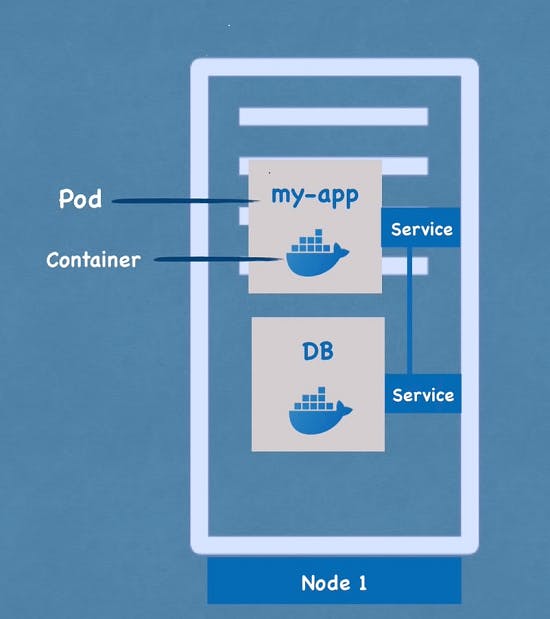
Services provide stable network identities for pods and are used to expose applications running in the cluster to external clients. Services provide a stable IP address and DNS name for pods, allowing external clients to communicate with the application even if the pods themselves are rescheduled to different nodes.
Types of Services
ClusterIP
A ClusterIP service is the default service type in Kubernetes. It provides a stable IP address and DNS name for pods, allowing external clients to communicate with the application even if the pods themselves are rescheduled to different nodes.
NodePort
A NodePort service is a service that exposes a specific port on the nodes in the cluster, allowing external clients to access the application directly. This type of service is useful when an application requires a static IP address or when it needs to be accessible from outside the cluster.
LoadBalancer
A LoadBalancer service is used to provide external access to an application running in the cluster. It provides a stable IP address and DNS name that is load balanced across the nodes in the cluster, ensuring that external clients can access the application even if one or more nodes are unavailable.
ExternalName
An ExternalName service is used to map an external DNS name to a Kubernetes service. This type of service is useful when you want to access an external service from within the cluster without having to create a load balancer or expose a cluster IP address
2. Ingress
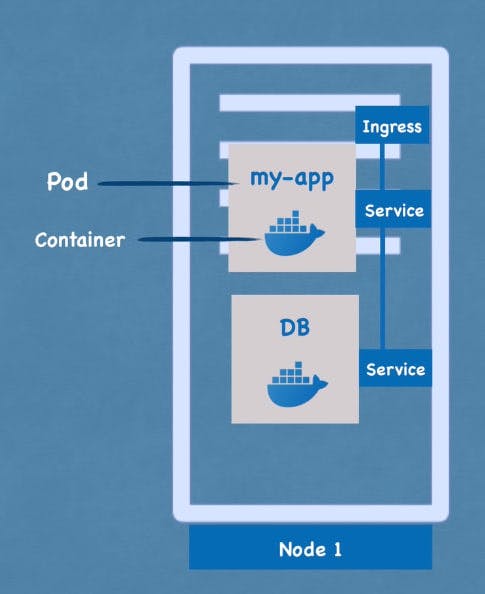
Ingress provides external access to services in a cluster. It defines a set of rules for incoming traffic, allowing incoming requests to be directed to the correct service based on the URL or hostname.
Ingress works by providing a single entry point for external clients to access services in a cluster. It acts as a reverse proxy, routing incoming requests to the correct service based on the rules defined in the Ingress resource.
Function of Ingress
Load balance incoming traffic
Ingress can be used to load balance incoming traffic across multiple replicas of a service, ensuring that the traffic is distributed evenly across the available resources.
Provide SSL termination
Ingress can be configured to provide SSL termination, allowing incoming SSL requests to be decrypted and redirected to the correct service in the cluster.
Provide authentication and authorization
Ingress can be configured to enforce authentication and authorization rules, allowing only authorized users to access specific services in the cluster.
3. ConfigMap
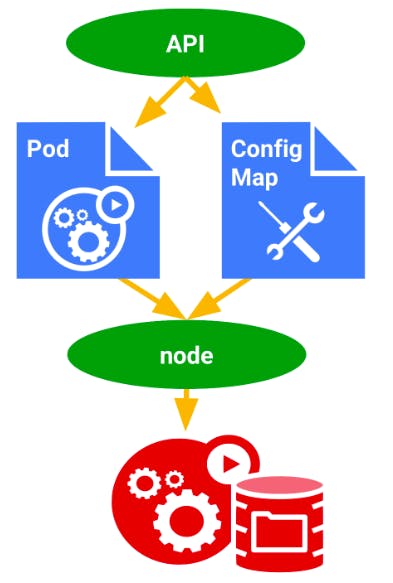
A ConfigMap allows you to manage configuration data for your applications. It provides a convenient way to store configuration data that can be easily referenced by your applications.
A ConfigMap is defined as a YAML file that contains key-value pairs. The keys in the ConfigMap can be referenced by environment variables, command-line arguments, or as files stored on disk. This allows you to manage configuration data in a centralized manner, making it easier to manage and update your applications.
ConfigMaps are useful in a number of ways:
Separating configuration data from code: By using a ConfigMap to store configuration data, you can keep configuration separate from the code of your applications. This makes it easier to update configuration data without having to update the code of your applications.
Sharing configuration data between applications: ConfigMaps can be used to share configuration data between multiple applications, making it easier to manage common configurations across multiple applications.
Making configuration data available to containers at runtime: The data stored in a ConfigMap can be easily referenced by containers at runtime, making it easy to manage configuration data for your applications.
4. Secret

A Secret allows you to manage sensitive information, such as passwords, tokens, and SSL certificates. It provides a secure way to store and manage sensitive information in a cluster.
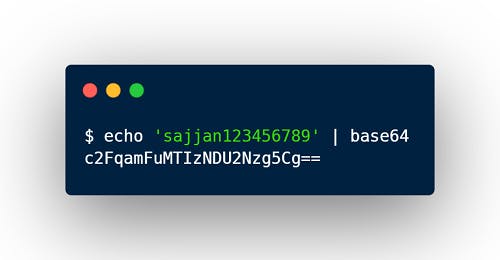
A Secret is defined as a YAML file that contains key-value pairs. The values in a Secret are encoded using base64 encoding, and they can be decoded by containers at runtime. This allows you to store sensitive information in a cluster without having to store it in clear text in your configuration files.
An Example of base64 coded password:-
5. Volumes
Volumes are a way to persist data in a Kubernetes cluster. They allow you to store data that needs to persist even after a container has been deleted, such as data that needs to be shared between containers or data that needs to persist even if the cluster experiences failures or restarts.
Type of Volumes:-
EmptyDir: An EmptyDir volume is created when a Pod is created and deleted when the Pod is deleted. It is useful for sharing data between containers within a Pod.
HostPath: A HostPath volume mounts a file or directory from the host node file system into a container. It is useful for sharing data between a container and the host node file system.
PersistentVolumeClaim: A PersistentVolumeClaim is a request for storage by a user. It is used to dynamically provision storage from a storage class.
6. StatefulSet
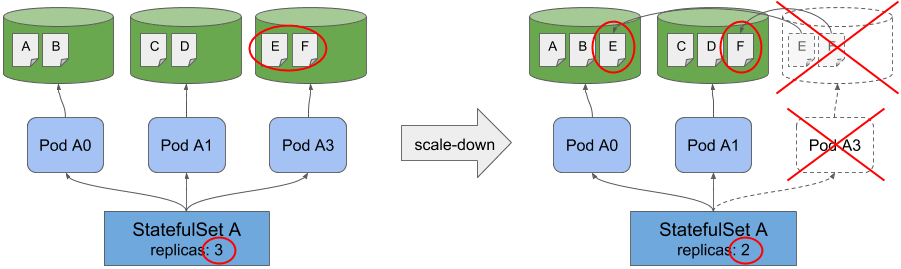
StatefulSets is used to manage stateful applications. A stateful application is an application that requires persistent storage, such as a database.
StatefulSets provide several key features to manage stateful applications in a Kubernetes cluster:
Stable Network Identities: Each Pod in a StatefulSet is assigned a stable hostname, which allows for the persistence of network identities across Pod restarts.
Persistent Storage: StatefulSets provide a way to manage Persistent Volumes (PVs) and Persistent Volume Claims (PVCs), which are used to store data persistently in a Kubernetes cluster.
Rolling Updates: StatefulSets provide a way to perform rolling updates to Pods, which allows for updating a stateful application without disrupting its operation.
7. Deployment
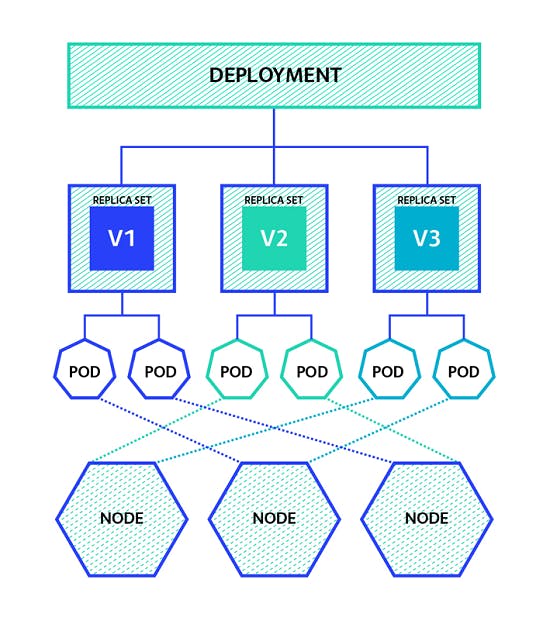
Deployment provides a declarative way to manage and update Replication Controllers and Pods.
A Deployment defines the desired state for a set of Pods and ensures that the desired number of replicas are running and available. In case of a failure, the Deployment will automatically recover the Pods to the desired state.
Features of Deployment
Rolling Updates: Deployments provide a way to perform rolling updates to Pods, which allows for updating an application without disrupting its operation.
Rollback: Deployments provide a way to roll back to a previous version of the application in case of a failure.
Scaling: Deployments provide a way to scale up or down the number of replicas of a Pod.
8. Labels and Selectors
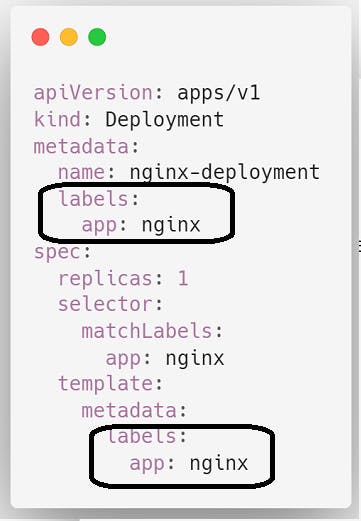
Labels and selectors are used to organize and identify resources in a cluster.
Labels are key-value pairs that are attached to resources such as Pods, Services, and Deployments. Labels can be used to describe the characteristics of a resource, such as its environment, role, or version.
Selectors are used to select a set of resources based on their labels. A selector is a set of label requirements, expressed as key-value pairs. For example, a selector can be used to select all Pods that have a label with the key "environment" and value "production".

